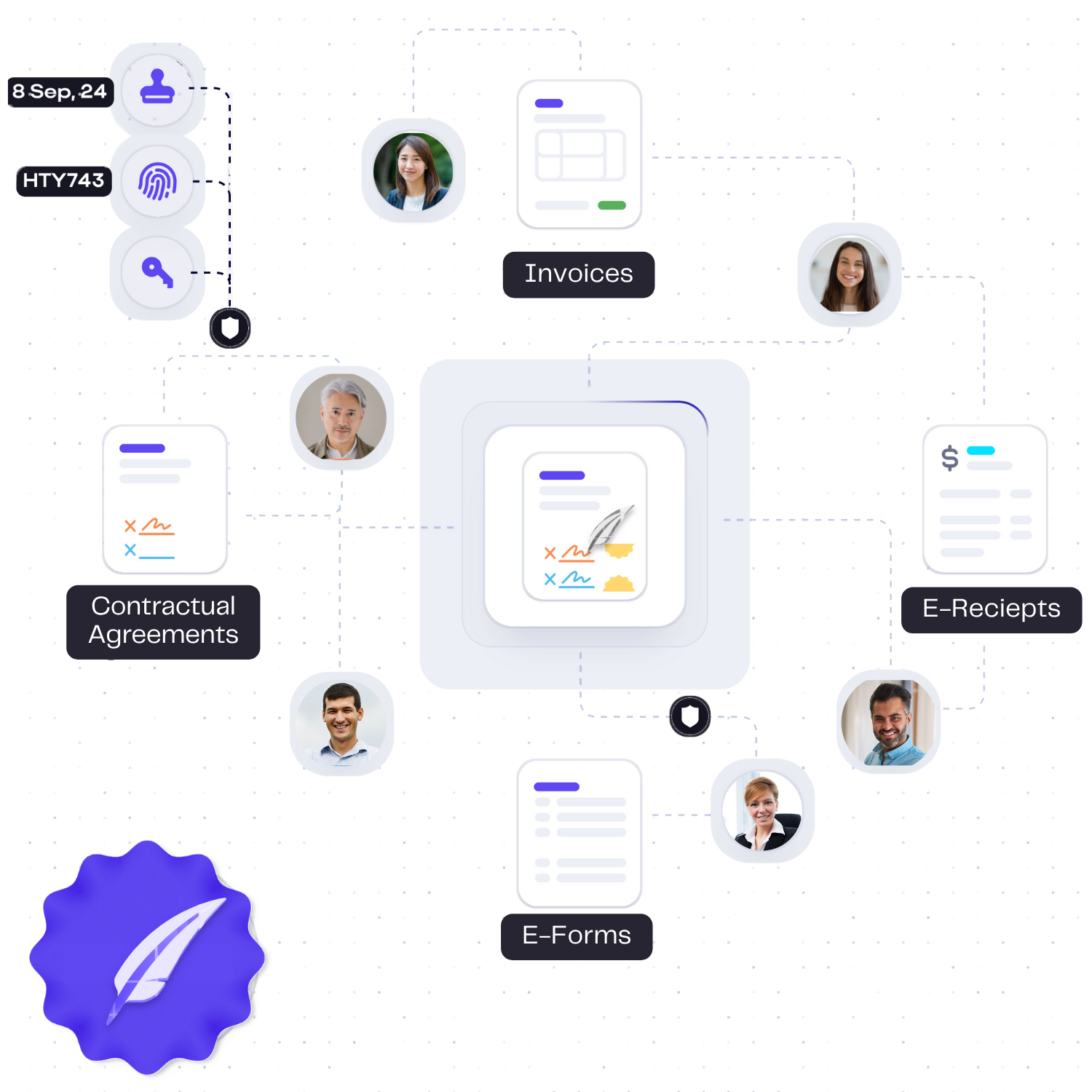
Your Digital Trust Infrastructure
YourDigitalTrustInfrastructure
SignVault delivers sophisticated document management with unmatched security controls, automated regulatory compliance, and complete data provenance tracking. Built for regulated industries where document integrity and verifiable trust are mission-critical.
Track, Nudge, Sign Feature
Track,Nudge,Sign
Integrated tracking functionality, providing an overview of the documents timeline. See all parties for pending, reviewed or completed status.
Helps keep track of individual missing signatures. Let SignVault nudge clients just in time for timely approval delivery deadlines.

Trust and Verification Features
TrustedDataProvenanceSolution
Verification and Proof of Authenticity through time based stamp verification explorer.
Easily prove the authenticity your data with our time seal verification ledger tool. Examine when the data was created and check if it is valid or not.
Immutable Proof for Every Digital Interaction
- Establish irrefutable document chronology with military-grade timestamp verification, backed by comprehensive data provenance tracking and temporal access controls.
- Maintain strict confidentiality while demonstrating document authenticity - our sophisticated ABAC framework enables granular verification without exposing sensitive information.
- Generate court-admissible audit trails on demand, with complete chains of custody powered by our proprietary data provenance system.
- Trust the future of digital evidence - SignVault's temporal validation is built on advanced cryptographic standards recognized by courts worldwide. Our timestamp certificates provide legally binding proof of document existence and integrity.
Enterprise Document Security Features
EnterpriseDocumentSecurity
Enterprise security and compliance automation for every step of your document journey.
Policy Driven Workflows


Cloud Document Workspace


Approval Admin Settings


Signature Process
SignatureProcess

Authentication
Real Estate Sell of a home, signing closing agreements.

Consent
Review and Accept, "Terms and Conditions Agreement".

Signatures Mark
Our delivery service notifies parties requiring signature.

Bind Signers ID to Doc
Collect and Bind IDs with E2E encryption mechanisms for privacy and security in mind.

Certify Lock Signature
Signed closing agreements are managed by trusted approving party.

Embedded Evidence
Each party inclusive in the document data signature ceremony holds a unique ID.

Timestamp Protocol Request
Encoded data is posted into digital ledger for Immutable Timestamp Registry.

Long Term Validation
Anyone with access to a SignVault doc can verify the provenance and authenticity.
Case Studies
SignaTrustSuite
Marketing
Real Estate Sell of a home, signing closing agreements.
Legal
Real Estate Sell of a home, signing closing agreements.
Human Resources
Real Estate Sell of a home, signing closing agreements.
Customer Success
Real Estate Sell of a home, signing closing agreements.
Operations
Real Estate Sell of a home, signing closing agreements.
Sales
Real Estate Sell of a home, signing closing agreements.
Pricing Plans
Choosetheperfectplantostreamlineyourdocumentworkflow
Individual
Get started with secure document management and basic e-signatures
- Single Admin Role
- 3 document workflows per month
- Basic document collaboration
- Basic audit trails
- Secure document storage (2GB)
- Standard e-signatures


Business
Advanced digital trust features for growing organizations
- Everything in Individual, plus:
- 2 Administrator roles
- Unlimited document workflows
- Advanced audit logging
- Organization-level security controls
- 12GB secure storage
- Enhanced e-signatures with PKI
- 1 organization (4 user accounts)
- 1 team workspace
- Role-based access control
Enterprise
Complete trust infrastructure for regulated industries
- Everything in Business, plus:
- Custom number of admin roles
- Custom storage options (S3 integration)
- Full Data Provenance System
- Advanced ABAC Framework
- Compliance Automation
- Custom Workspaces
- Enterprise Features
- Data retention policies
- Add users: $9/user/month
- Add teams: $3/team/month
Frequently Asked Questions
FAQ's
Here are some of the most commonly asked questions by our users. These questions cover a variety of topics that many people have found helpful.
JointhePublicWaitlistforOrchastra
We are building a new and easiest way to create domain-specific AI agents. Only the first 100 people who sign up will get lifetime free access to Orchastra.
4.95/5
Based on over 256+ reviews